
What is IP spoofing?
Attackers use IP spoofing to manipulate data packets and paralyze entire companies. Every second company in Germany has already been affected by industrial espionage, sabotage
Your IP is: 3.147.68.89 – ISP: Amazon Technologies Inc. – Your status: Unprotected
Your IP is: 3.147.68.89 – ISP: Amazon Technologies Inc. – Your status: Unprotected
Your IP is: 3.147.68.89
Internet provider: Amazon Technologies Inc.
Your status: Unprotected

Attackers use IP spoofing to manipulate data packets and paralyze entire companies. Every second company in Germany has already been affected by industrial espionage, sabotage

Our Data were in the past disproportionate used. The desire to Privacy and the turning away of the total Transparency stand at Focus: The human

Privacy means having an overview of one’s own situation, being able to express oneself freely, knowing which audience is listening and how information spreads. Hide

VPN for gaming VPNs (=Virtual Private Networks) offer you more protection on the Internet. Your IP address is obfuscated. VPNs are used for streaming, protection

A reflective guide to setting up a fixed IP address including benefits and vulnerabilities. Information technologies are an integral part of our lives. Our smartphone

On the Internet, activities are more or less visible: whether you shop online, send e-mails, or stream your favorite show – you always leave a
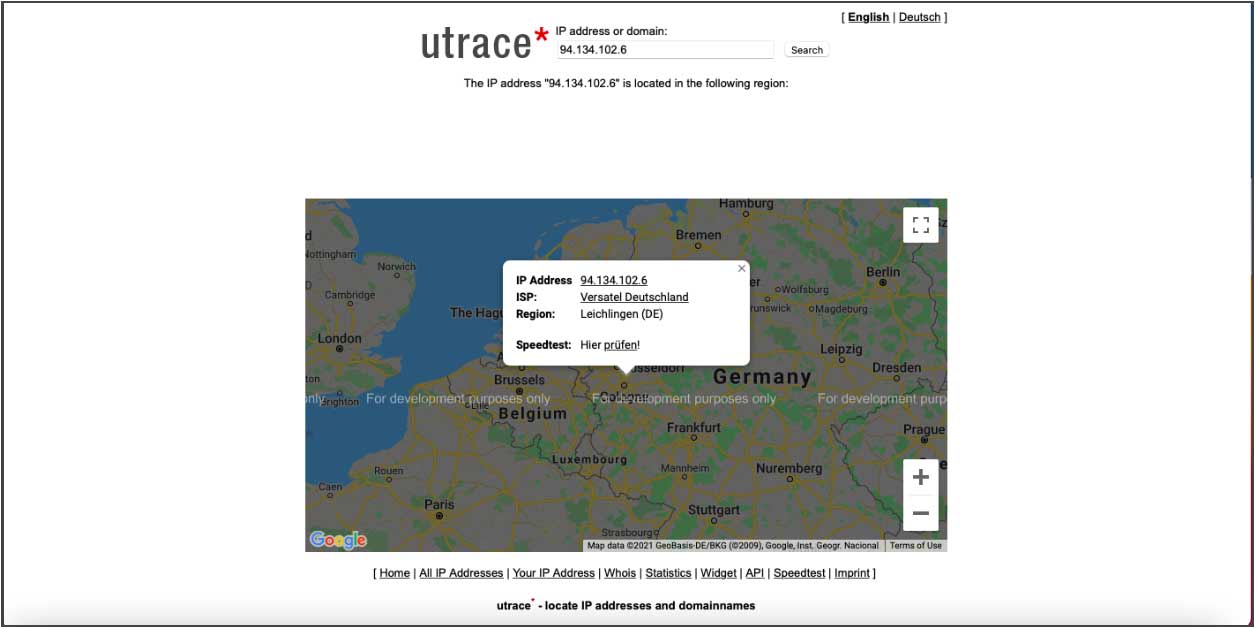
What is my IP? With this tool you can find out what your public IP address is. The tool displays your location or the address
Digital privacy should be protected in any case, whether with Tor, proxy or VPN. It is important to protect yourself and preserve your anonymity on

Is Your Robot vacuum cleaner from Hacking-attacks protected? Who many internet-enabled Devices owns, should itself especially protect. What is a VPN Router? A VPN router

We’ve already reported on what three popular ways to to IP addressobfuscation there are: Tor browser, proxy and VPN. We assume that there is a




Sie erhalten von uns keinen Spam. Wir senden Ihnen Informationen zu unseren Produkten und über den sicheren Umgang im Internet.

IPv4: A protocol standard The fourth version of the Internet Protocol is called IPv4. Each IPv4 consists of a twelve-digit number e.g. 139.7.147.49 and runs

Is Your Robot vacuum cleaner from Hacking-attacks protected? Who many internet-enabled Devices owns, should itself especially protect. What is a VPN Router? A VPN router

Attackers use IP spoofing to manipulate data packets and paralyze entire companies. Every second company in Germany has already been affected by industrial espionage, sabotage

A supposed sense of security protects not from leaks. With this Leak Tools makes DNSLeaks locate and protects the own privacy. VPN-Security test: With this
PrivacyPhone
PrivacyNet
VPN client
Functions
Use cases
What is a VPN
Prices
VPN Security Check
Display & locate routings
VPN free test
FAQ
Contact
Help Center
Affiliate Area
Press center
2021 Copyright DN8.co. All rights reserved.